Keeping fuel moving safely, reliably, and securelyFor over 75 years, UK fuel distributors like yours have built their reputation on reliability. When customers need fuel, it arrives — safely, compliantly, and on time.
Today, that reliability depends on more than tankers and depots. It depends on the digital systems that plan, authorise, load, route, and account for every delivery.
Downstream fuel supply is now a cyber‑physical operation.
A disruption to systems doesn’t just affect screens and spreadsheets — it can:
delay or stop loading,
send vehicles to the wrong location,
interrupt emergency or time‑critical deliveries,
create safety, environmental, or regulatory exposure.
That’s why cyber resilience for fuel distributors isn’t about “IT hygiene”. It’s about operational continuity, safety, and trust.
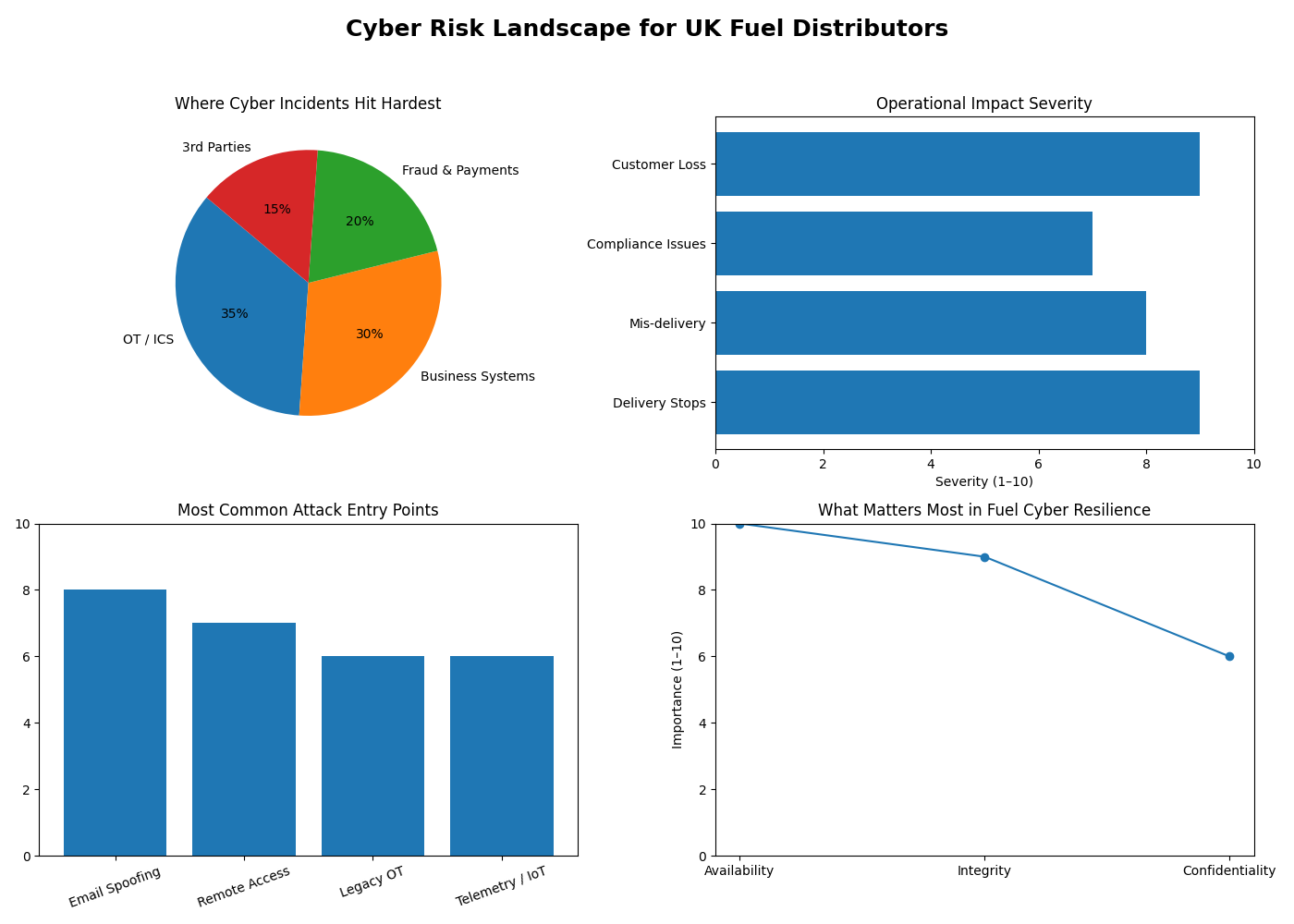
1) Where cyber incidents hit hardest
The pie chart shows that OT / ICS and core business systems dominate real‑world impact — reinforcing that this is not just an “IT problem”, it’s an operations and safety issue.
2) Operational impact severity
This horizontal bar chart ties cyber events directly to:
delivery stoppages,
mis‑deliveries,
compliance headaches,
rapid customer loss.
“Even a ‘small’ IT incident can score a 9 out of 10 when it stops trucks loading.”
3) Most common attack entry points
This graph visually reinforces that attackers usually enter through:
email spoofing,
remote access,
legacy OT,
telemetry / IoT.
“Attackers don’t break in through pipelines — they walk in through email and remote access.”
4) What actually matters in fuel cyber resilience
This final chart deliberately flips the usual cyber narrative:
Availability first
Integrity second
Confidentiality third
“In fuel distribution, availability beats confidentiality — because fuel not moving is the incident.”
Why fuel distributors are different
Unlike typical office‑based businesses, downstream fuel suppliers operate across terminals, depots, vehicles, drivers, and third‑party systems.
That creates risks most cyber providers don’t understand.
What makes fuel distribution uniquely exposed ?
Operational technology (OT) environments
Pumps, tank gauging, loading automation, blending systems, and safety controls often run on long‑lived, fragile systems where downtime or incorrect data has real‑world consequences.
Time‑critical delivery chains
If systems are unavailable, drivers don’t wait — and customers don’t either. Even short outages can trigger lost business.
Email and instruction‑based operations
Delivery changes, emergency drops, release notes, and authorisations often rely on email or mobile instructions — prime targets for spoofing and fraud.
High‑value, repeat transactions
Fuel is a predictable, high‑volume commodity. That makes billing systems, fuel cards, and B2B accounts especially attractive to attackers.
Interconnected ecosystems
Hauliers, terminals, telemetry providers, card processors, and OT vendors all connect into the same operational picture — increasing third‑party risk.
Translating cyber issues into business pain
When something goes wrong, the impact isn’t theoretical
Deliveries stop
If dispatch, billing, or release systems are unavailable, loading often pauses — even if tanks are full.
Fuel goes to the wrong place
Spoofed or altered instructions can result in mis‑deliveries that look legitimate on paper but are unrecoverable in reality.
Compliance questions appear fast
HMRC, insurers, and customers want evidence: records, logs, controls. Missing or corrupted data becomes a second crisis.
Customers switch quickly
Fuel buyers don’t wait for recovery updates. Reliability failures spread fast in local and rural markets.
Recovery costs exceed the fuel value
Overtime, re‑routing, refunds, chargebacks, investigations, and reputation damage often outweigh the value of the lost load itself.